
Close



Public key and private key are used as a pair. A public key is a long string of numbers used to encrypt information. The public key can be published publicly because it is only used to encrypt information and cannot be used to decrypt information. The private key is also a long string of numbers used to decrypt information encrypted with the public key. The private key must be kept secret because anyone with access to it can decrypt the encrypted information.
In this article from Pooyan Music, we are going to review the concept of public key and private key and then compare and review their use.
Public key and private key are used for a wide variety of applications. In the following, we mention these uses and explain each one.
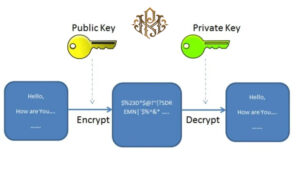
Public key and private key are used in email encryption to create a secure communication channel. In this method, the sender uses the receiver’s public key to encrypt the message. The receiver will then use his private key to decrypt the message.
In this way, only the intended recipient can read the message. Even if someone gets access to the encrypted message, they cannot decrypt it because they do not have the private key.
Encrypting a file using a public key and a private key is a relatively simple method that can significantly improve the security of your files. Public key and private key are used in file encryption to encrypt and decrypt sensitive files. In this method, the sender uses the receiver’s public key to encrypt the file. The recipient then uses their private key to decrypt the file.
Here are some examples of public key and private key usage in file encryption:
Public key and private key are used in digital signature to verify the authenticity of a message or document. In this method, the sender uses his private key to create a digital signature. The receiver can then use the sender’s public key to verify the authenticity of his digital signature. If the digital signature matches the sender’s public key, the receiver can be sure that the message or document was sent by the original sender and has not been tampered with.
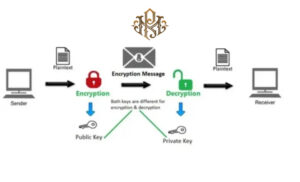
Public key and private key are used in secure communication to establish a secure communication channel. In this method, the sender uses the receiver’s public key to encrypt the message. The receiver then uses his private key to decrypt the message.
In this way, only the intended recipient can read the message. Even if someone else gets access to the encrypted message, they won’t be able to decrypt it because they don’t have the private key.
Public key and private key are used in authentication to verify the identity of a user. In this method, the user uses his private key to create a digital signature. The authentication system can then use the user’s public key to verify the authenticity of the digital signature.
If the digital signature matches the user’s public key, the authentication system can be sure that the user has verified his identity.
To use the public key and private key in authentication, the user must store his private key in a safe place. The authentication system must also have the user’s public key.
To use public key and private key in different applications, sender and receiver must have each other’s public keys. These keys can be exchanged directly between two users or distributed through a public key server (PKI).
Public key and private key are important technologies used for a wide variety of applications. This technology allows users to securely store their information, encrypt their communications, and verify their identity.