
Close


What is Sibyl attack? Familiarity with Sybil Attack Sybil attack refers to the use of a node to execute fake identities simultaneously in a peer-to-peer network. The main goal of this type of attack is to weaken the authority in a trusted system by gaining majority influence in the network. Fake identities serve to create this influence.
A successful Sybil attack gives threat actors the ability to perform unauthorized actions on the system. For example, it enables a single entity such as a computer to create multiple identities, including user accounts and accounts based on IP addresses. All these fake identities deceive systems and users and pretend to be real.
The name of this attack was inspired by a book in 1973 called Sybil. The subject of this book is about a woman who has dissociative identity disorder. The term Sybil in the context of attacks was first coined by Brian Zill and discussed in an article by John R. Douceur on Microsoft Research.
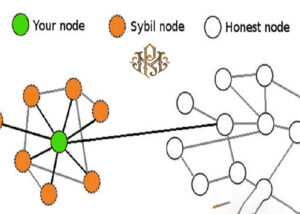
The main goal of Sybil attacks on blockchains is to gain disproportionate influence over the decisions made in the network. The Siebel attack is one of the most important cyber attacks that, if successfully carried out, will create very serious challenges, some of which are impossible or expensive to fix. If the attackers can successfully carry out the Sybil Attack, there are two very important problems that will arise:
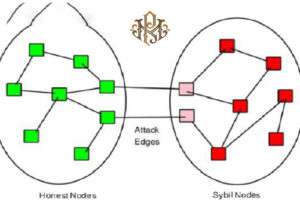
On the Bitcoin network, many decisions affecting operations are voted on. By voting, the miners and those who maintain the nodes of the network determine the number of people in favor and against the decisions. If attackers create multiple identities in a network, they can control any number of identities and vote.
Also, Sybil Attack has the ability to control the flow of information in a network.
For example, a mustache attack on the Bitcoin network can be used to obtain information about the IP address of a user connecting to the network. This compromises the privacy, security and anonymity of web users. The only task of attackers is to take control of nodes in the network, collect information from nodes and create new fake nodes. As such, their fake identity work begins.
Sybil attack on Tor network Tor network works on a peer-to-peer model.
This network allows nodes to surf the Internet anonymously. However, if a malicious entity or spy takes control of tens, hundreds, and thousands of nodes, it can compromise the privacy of the network. Once both the input and output nodes are controlled by attackers, they can monitor everyone’s network traffic.
Considering the problems Sybil attack can cause, it should be prevented from happening. There are various ways to prevent these attacks, each of which can significantly reduce the probability of a Sybil Attack. Some Sybil Attack prevention methods that have a higher percentage of confidence than other methods are: Rely on, they may still be vulnerable to Sybil attacks.