Consensus Algorithms in digital currencies play a very important role in ensuring the security and accuracy of network performance. In the following, we will briefly review some common consensus algorithms in digital currencies:
- Proof of Work (PoW): PoW is one of the most widely used consensus algorithms used in currencies such as Bitcoin. In this algorithm, miners compete to solve a complex problem and consume a lot of computing resources (such as processing power). The first miner to solve the problem is declared the most valid block and is awarded a reward (usually cryptocurrency). This algorithm faces high security and high cost of data manipulation.
- Proof of Stake (PoS): In PoS, the right to issue a new block is based on the amount of digital currency that a person has available. In other words, participants who keep a larger amount of currency in their wallet have a higher probability of selecting the next block. This algorithm has the least consumption of computing resources compared to PoW, but it can have consequences for more concentration in the hands of owners.
- Delegated Proof of Stake (DPoS): DPoS is a type of PoS in which participants choose by appointing delegates and giving them the right to choose new blocks. Agents are responsible for generating blocks and receive rewards for it. DPoS is faster than PoW and PoS, but may lead to concentration of power in designated devices.
- Proof of Authority (PoA): In PoA, trust is involved instead of solving problems using computing resources. Multiple validating agents determine which blocks are valid and approve new blocks.
An overview of consensus algorithms in digital currencies:
- Practical Byzantine Fault Tolerance (PBFT): PBFT is a vote-based consensus algorithm that is used in distributed networks with the presence of malicious (Byzantine) agents. In this algorithm, certain roles are determined as the chairman and members of the committee. To make a decision, committee members vote and based on the majority of votes, the decision is made. This algorithm provides high speed and fault tolerance, but allows a limited number of malicious agents.
- Proof of Elapsed Time (PoET): PoET is an algorithm designed for distributed networks with limited computing resources. In this algorithm, participants randomly execute computing resources for a certain period of time (time pattern). A participant who executes a smaller time creates the new block. PoET is rewarded per block to the participant who spends the least amount of time.
- Proof of Burn (PoB): In PoB, participants must burn some digital currency and earn the right to document the block as proof of its burning. By burning the currency, its amount is removed from the flow documents and they receive rewards. Due to the need to burn the currency, this algorithm can lead to a decrease in the currency balance and an increase in its value.
Also, many digital currencies use a combination of algorithms and consensus mechanisms, and each has its own characteristics and strengths and weaknesses. Choosing the right consensus algorithm is very important depending on the needs, purpose and characteristics of the desired digital network.
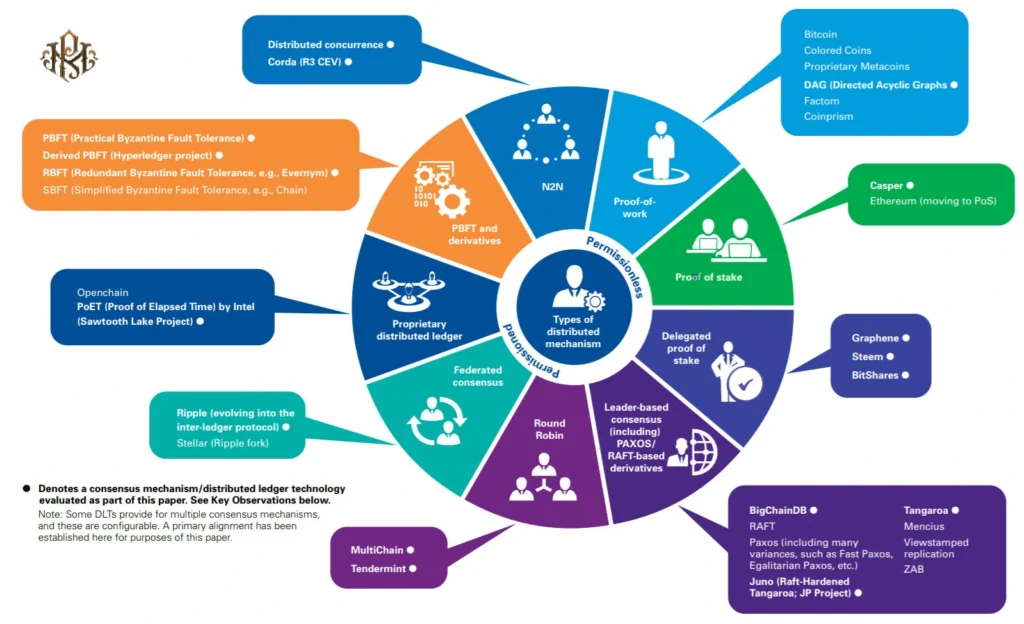
An overview of all consensus algorithms in digital currencies
In general, consensus algorithms are used in cryptocurrencies to reach agreement and consensus on the state of the network, verify transactions, and generate blocks. These algorithms play a very important role in the security and correctness of the network operation and are directly affected by the resource budget (such as processing power and digital currency) and network structure.
Some of the common consensus algorithms in digital currencies are:
- Proof of Work (PoW): In PoW, miners compete to solve a complex problem using their computing resources. The first miner to solve the problem creates the new block and submits it to the network. This block is then verified by other participants and finally added to the block chain. PoW is used to provide security in the network, but requires high energy consumption.
- Proof of Stake (PoS): In PoS, the right to issue a new block is based on the amount of digital currency that the participants have available. In other words, participants who hold a larger amount of currency have a higher probability of selecting the next block. Compared to PoW, PoS requires the least consumption of computing resources and ensures the security of the network through the preservation of digital currency.
- Delegated Proof of Stake (DPoS): DPoS is a type of PoS where participants choose delegates and give them the right to choose a new block. Delegates are responsible for generating blocks, and based on majority votes, new blocks are approved. DPoS has a higher block generation speed and leads to the concentration of power in designated devices.
- Practical Byzantine Fault Tolerance (PBFT): PBFT is an algorithm used in situations where malicious agents are present.




